Mifare Cracking Android
What’s NFC-War? It’s the previous project which mfoc-like application for Android/ BlackBerry Phone, and re-named as NFC-War. It could be installed in Android/ BlackBerry Phones with NFC function to detect Miafre Classic vulnerabilities, we call it a swiss knife of Proxmark3. I don't uderstand: is this a DEMO app or is just a 'pre-release' of the full app? In few words, is this a free app or do you provide a paid app? How much will it cost? Do you plan to provide read/write support also for ISO14443B standard?
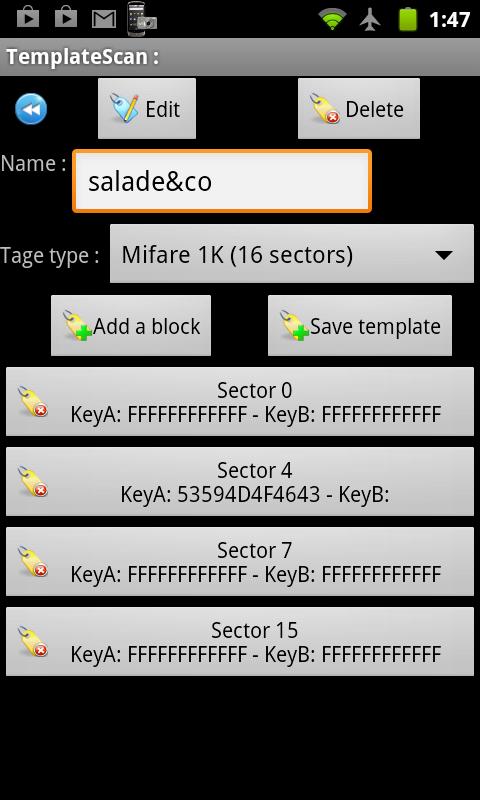
The BlackHat slide deck from 2007 that you linked to contains a very good description of cracking Mifare Classic. Slide 23 talks about how MFOC and MFCUK are used in sequence: MFOC recovers all keys given a known key. The attacker uses MFOC to first test against all the previously-known keys. Jul 15, 2013 Access Control – Part 2: Mifare Attacks. Android NFC Apps. (sufficient for reading / cracking / writing / cloning Mifare Classic cards).
Install does not work in bluestacks (android emulator) and it installs but crash at opening in a real device non-NFC I tested; I will test it in an enabled NFC device soon. Free for ALL! Function is actually complete,MayBe will support for ISO1444EB standard。 remember only for Android NFC Phone/Pad. Hi @ikarus, thanks for your prompt reply and the link. Yes ofcourse, this is the whole reason I spent my scholarship stipend money on a PM3 board. As I was saying, I have gotten the NFC emulation mode activated on my Nexus S JB build. I can read blocks using PM3.
My other SCL3711 reader detects Nexus-S too as a Mifare 4k. But I am still unable to write in any of the blocks. If you happen to find any information around that, please share.
Can you please tell us how did you do the full emulation? Are you able to set the blocks with whatever you want?
A subreddit dedicated to hacking and hacking culture. What we are about: quality and constructive discussion about hacking and hacking culture. We are not here to teach you the basics. Please visit for posting beginner links and tutorials. Hacking related politics welcome. Penalty table: Offense Penalty Spam/Clickbait Permanent ban. 'How to hack (x)/Help me hack (x)' type of questions 30 days ban.
Aiding those who want help to hack anything 5 days ban Sharing private data (dumps etc.) 15 days ban Rules • WE ARE NOT YOUR PERSONAL ARMY • Questions and discussion prompts should be geared towards intermediate to advanced hackers. Ehci Driver Installation Disk Windows 98. • Requesting help/instructions on how to hack anything will be met with ridicule and a ban. Also, nobody cares if you got hacked. Vodburner Serial Key Free Download.
Sorry, have a better password. • Aiding those who are looking for help to hack anything will be banned. • Sharing Private data is forbidden (no IP dumping). • Spam is strictly forbidden and will result in a ban.
(Spam as in links that violate the spam guidelines ) • Off-topic posts will be treated as spam. • Jail-breaking and rooting of phones and posts that aren't directly related to mobile security should be directed to other subreddits such as. • Off-topic or surly responses will be removed (a cryptographic hash!= potato hashes). • Want to learn 'How to hack'?, Please head on to as questions about 'how to hack' anything aren't allowed here.
IRC Note: if no one answers immediately, stick around and someone will read it. Recommended Subreddits: • • • • • • • • •. Hey Hacking whats up? I was thinking the other day that what if it was possible to program android devices capable of NFC (Near Field Communication) to unlock RFID enabled doors. RFID and NFC both operate in the same frequency bands, so would it possible to design an app that spoofed the lock? I have little understanding of how the the identification system works and how the system verifies whether someone is legit.
But it seems plausible to me. Also, anyone else have any information on NFC hacking, like installing mal-ware software on mobile devices without permissions. I've seen some videos, but haven't seen anything relevant. If the door used the same frequency that NFC uses (13.56 MHz), and the door only looked at the information written to the card, then it's possible. If you had access to the card, then you could easily spoof the door in this situation. However, I imagine people who make locks are a little more clever than this. I'm not sure exactly how it's done, but I believe that some keys may actually shift codes each time they are activated.
Electronic garage door openers used to have similar problems until they implemented this solution. Some information - In my experience, the 13.56 MHz RFID chips most commonly have 1KB of data storage, in addition to a read-only serial number.
Spoofing the serial number may be impossible for an app (as that may be handled on a lower level by the phone), but could be done with your own handmade device. The 1KB of storage can hold a looong key, so brute forcing is impractical. Finally, I believe there may be more security embedded into the cards that I haven't got around to reading about yet, which may have to be compromised first. Oh, and remember, this is only for the 13.56 MHz cards, so NFC may be completely incompatible. If you're interested, look around online - all of this information is easy to find.
My first step would be to write an app to get the raw data the card is transmitting, and see if it changes. Try repeating it from the app to the door, see if that works. If you phone doesn't like it, you could try building your own reader/writer from something like, or its component parts. Read the datasheet. Experiment and be curious! Thanks man for the comment!
I have been working through some New Boston tutorials on Android programming ( ), I've gone through like 50 so far. Still a novice, but learning fast. I think it would be an exciting first real app project. Thinking about buying a Nexus 4 hopefully in the next month to develop on and use.
I couldn't find squat specification on the Nexus 4 NFC chip, but I did find that many 'signature' lock systems work off of 13.56 Mhz., and are compatible with NFC! However, what I've read so far about RFID locks, cloning will not work. And even emulating it will be tough, Google doesn't include anything in their SDK to help you out with that. It would be interesting to see the data the RFID card submits as well as the card reader itself. What information is passed back an forth.
If any from the card reader. I believe NFC is passive, meaning that it can't read information off of cards, there has to be some sort of fluctuating magnetic field to go through the card in order for information to be read. Wow, that website's awesome - thanks.
The lack of SDK support was what I was referring to with being unable to spoof a serial number. That's the great part about building systems from scratch, you can make them work the way you want them to, as opposed to how they should work. On the other hand, it can get complicated and difficult.
NFC is not entirely passive - technically, no RFID is. One of the communicating devices has to provide power, making it active. With NFC tags or cards, the phone/reader is active, and is generating that electromagnetic field which provides enough power to the tag to have it transmit something back. The has information on this as well, if you look under 'Essential specifications'.
The entire article is useful, though. Most RFID systems nowadays are 13Mhz (mostly Mifare DESFire/Plus), so technically you can communicate with them using an Android NFC device because the underlying protocol and technology is pretty much the same. It won't open doors for you though – the authentication works by challenge-response and all communication is encrypted, so without the secret keys you're out of luck. One exception are Mifare Classic cards – which are still VERY common – the encryption (Crypto1) has been broken by hardware reverse-engineering some time ago (surprise! Almost as if security by obscurity doesn't work). This means that you can easily crack the keys for pretty much any card. This would allow you to copy and clone a card from someone who has access.
Now for the Android part: the framework doesn't give you enough low-level access to simulate a Mifare card with the correct timing, but for a few devices there was some progress on this: • • • •.